Everything You Always Wanted to Know About HIPAA* (*But Were Afraid to Ask)
By Rock Health intern Jessica Hershfield
Last Thursday, Rock Health hosted HIPAA specialist Stefano Quintini, of Fenwick & West, to help our entrepreneurs maneuver through the sticky issues associated with HIPAA. When and how HIPAA applies to health-tech companies is complex and confusing, and often full of stereotypes. Stefano tackled these difficult gray areas by first outlining what HIPAA actually applies to: covered entities and business associates.
Covered Entities (CE): health plans, healthcare providers, and healthcare clearing houses
Business Associates (BA): anyone who performs functions on behalf of covered entities that involves personal health information
So, now that we know who may be liable under HIPAA, let’s look at what is covered.
Protected Health Information (PHI): Any information that relates to the individual’s health or condition, information on the provision of healthcare to the individual, or information regarding the payment for the provision of healthcare to the individual.
Personally Identifiable Info (PII): Data such as name, address, social security number, etc.
In order for HIPAA to be applicable, both PHI and PII must be present, in conjunction with a CE. Here are a few case studies:
Case 1: An application that provides personal fitness data to the user
In this situation, a vast amount of PII exists; however, no PHI exists (only fitness data, which is provided solely to the user) and therefore, this is not covered by HIPAA.
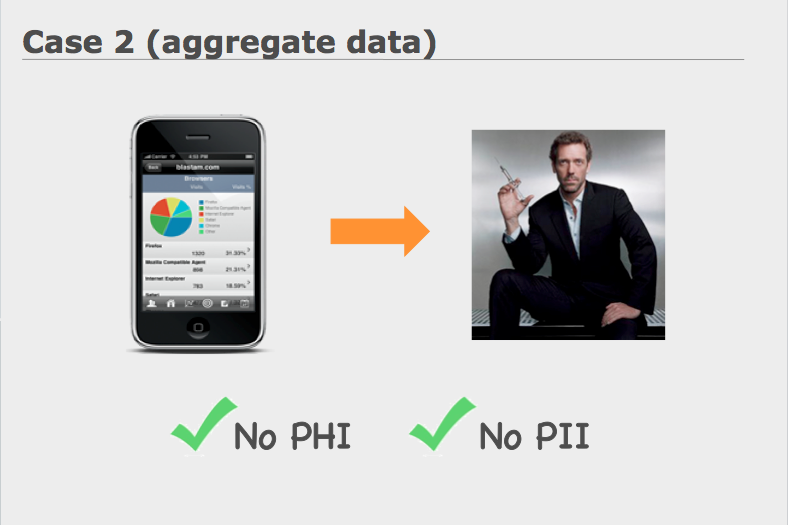
Case 2: An application that takes their users healthcare data, and provides it to physicians in aggregate form
Under this case, there is no PHI or PII, since no single user can be identified from the aggregated data, and therefore, HIPAA once again does not apply.
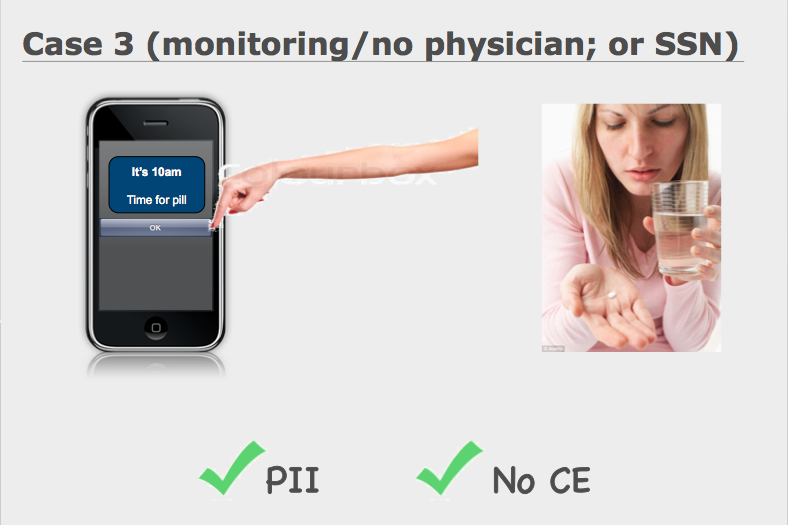
Case 3: A monitoring application that reminds patients to take their medications in a timely manner
In this situation, there is PII and PHI; however, since there is no covered entity involved, and the information’s final destination is the user, HIPAA has no reign.
Case 4: A monitoring application prescribed by a physician, or an application that provides data to the physician
Under these conditions, there is PII and PHI, which is provided to covered entities; and therefore HIPPA applies.
So what if you have an application enforceable under HIPAA? There are a few strict rules that must be followed in order to be HIPAA-compliant.
Privacy Rule:
Applicable to all CEs, the use of PHI other than for treatment, payment, or healthcare operations is strictly forbidden unless written authorization is obtained. For more detailed information on the Privacy Rule, look here.
Security Rule:
This rule, pertinent to all CEs, covers the standard safeguards related to health data. This rule deals with the administration, physical, and technical aspects underlying healthcare data. For example, how the data is stored, how the administration documents the data, and how the data is encrypted. While there are many required aspects to this rule, the standards are flexible; and it is important to understand the required versus addressable standards. Finally, it is very important to notify the HHS in the event of a breach of security. Read more here.
These obligations apply to all CEs. But you may be wondering how the BA fits into HIPAA policies. According to Stefano, there is one golden rule that all BAs should follow: the BA can’t cause the CE to breach its HIPAA obligations.
BA obligations:
Required to enter into business associate agreement with CE.
After the HITECH Act:
Comply with HIPAA’s business associate safeguards on use restrictions
Comply with Security Rule
Notify CE in case of breach
Read more information on BA obligations, in addition to sample BA contracts, here.
HIPAA is a complex subject that’s impossible to completely cover in an hour’s time. However, we hope this introduction will lead our start-ups (and yours) to the path of successful compliance.